This blog post originally appeared on crypto.is. We've since shut down that website, so I have copied the blog post back to my own for archival purposes.
There are two main implemented remailer networks in operation: Mixmaster and Mixminion. Mixmaster was written in the early 90s by Lance Cottrell, and was maintained for a number of years by Len Sassaman. Mixminion was written in the early 2000s by Nick Mathewson, based on a research paper he wrote with George Danezis and Roger Dingledine. A third, Cypherpunk Remailers, exists as well, although is mostly supported as a compatibility layer in the Mixmaster software. Although conceptually they all do the same thing - allow the sending of anonymous emails - there are a number of design and implementation differences.
In Mixmaster, when you compose your russian-doll nested messages to each remailer, you will send the message to the first node using normal email - SMTP. Each node will subsequently send it to each following node using an email message over SMTP.
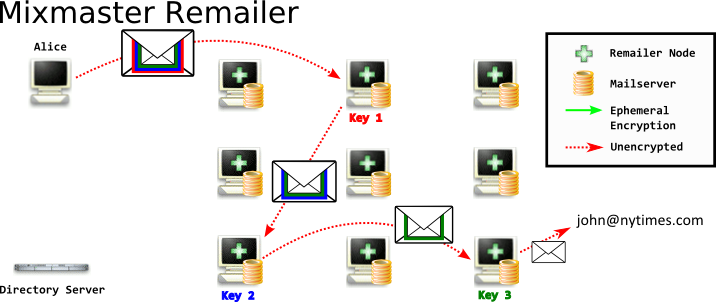
There disadvantages of this.
- The SMTP conversation between you and the first node is not encrypted. An attacker observing you would know you are sending messages to a remailer, even if they did not know remailers existed, or had a list of them. It's important to note that the message is still encrypted, but the transport of the encrypted message is not itself encrypted.
- The SMTP conversation between each node is not encrypted. This allows an attacker to observe the encrypted messages sent between. The attacker could store the encrypted messages for later decryption if they compromise the server's private key.Again, the message is still encrypted, but the transport of the encrypted message is not itself encrypted. There are some technicalitys with StartTLS and DHE ciphersuites, but these should not be relied on.
- Each Mixmaster node must run an email server. While running a webserver such as Apache or Nginx is very common today, and there are a lot of guides and best practices around doing so - running a mailserver today is more esoteric. The guides are less common and more out of date - it is not a common skill.
However, in Mixminion, when you compose your nested message, you will send the message to the first node using a binary protocol inside a SSL connection. That SSL connection uses Ephemeral Encryption - which provides Perfect Forward Secrecy (PFS). PFS means that if an attacker compromised the server's SSL certificate - they would not be able to decrypt that conversation. And, if an attacker breaks that conversation - they cannot read any other conversation. This is a very nice and robust property to provide, and by using SSL as a transport mechanism - we get it essentially for free, without having to write any additional code.
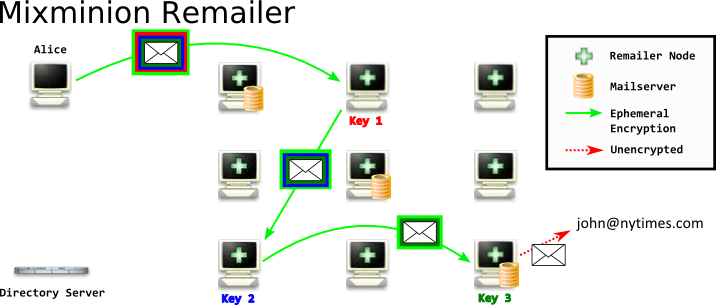
The advantages of Mixminion's approach compared to Mixmaster's:
- The conversation between you and the first node is encrypted using SSL. Although an attacker who had a list of all remailer nodes would know you were speaking to one, an attacker who did not would see a normal SSL connection, extremely common on the web. With additional development, it would be possible to deploy 'bridge' Mixminion nodes, similar to Tor bridges, that an adversary was unable to enumerate.
- The conversation between each node is encrypted with SSL using an ephemeral handshake. An attacker who observed the conversation can only know they are transmitting remailer messages if they know the computers are remailers a priori. Because the conversation is encrypted ephemerally, an attacker cannot coerce an operator to decrypt a traffic intercept later.
- Only the exit Mixminion node must run an email server. Because the nodes pass messages between themselves using a binary protocol inside of SSL, and not via email messages, the only node that must run an email server is the final node when the message exits the remailer network and enters normal email. While some Mimixion nodes must run email servers, many do not need to.
Another major difference between Mixmaster and Mixminion is that Mixmaster is one-way. You can send an email anonymously to an individual, but if you want them to be able to reply, you would have to give them a reply address. Even if you choose a free email service and lie to them about your real name - this can still de-anonymize you, for example through a subpoena to the email provider. Mixminion however allows replies through what are called 'Single Use Reply Blocks' or SURBs. When I receive a message with a SURB, I can reply to the sender without know who the sender is. We'll talk more about SURBs and reply-block based designs later also.
There are a number of other differences between Mixmaster and Mixminion, including directory services, exit policies, dummy traffic. And there are a number of other topics and developments in anonymous email including packet formats (like Sphinx) and nym-based reply methods (like Pynchon Gate). We'll be covering more about these topics in the future.
Finally, before signing off, it's important to note that there are practical issues with both Mixmaster and Mixminion today. Neither one of these should be relied on for strong anonymity. Mixmaster, for example, makes use of 1024-bit RSA keys; and Mixminion has not been actively developed for years.
This blog post is licensed under Creative Commons Attribution 3.0 United States License and is inspired by, and makes heavy use of, the images produced by the EFF & Tor Project here.
required, hidden, gravatared
required, markdown enabled (help)
* item 2
* item 3
are treated like code:
if 1 * 2 < 3:
print "hello, world!"
are treated like code: