I don't write a lot, so when I do write for another blog (usualy an employer's) I tend to go to pains to copy the blog post here (with a credit). Today I've published five technical blog posts for another blog, but I'm not reposting them - I'm just pointing at them. They're hosted on the same machine as this one, just on a seperate domain, so I'm not worried about losing them.
Crypto.is kicks off its blog with a series of articles about remailers! This is the first several installments in what is intended to be a series on how remailers work, the theory behind them, and many of the choices that must be considered. Some of the topics we intended to dive deeply into in the future is how to have a directory of remailer nodes, how to handle messages that overflow the packet size, more details on Mixminion, as-yet-unimplemented Academic Papers (like Pynchon Gate and Sphinx), and more! Check out posts One, Two, Three, Four, and Five. The comments section should work, so please do leave comments if you have questions, insights, or corrections!
These blog posts are:
| 5 | A Tagging Attack on Mixmaster | 05 Jan 2013 23:48:00 EST by Tom Ritter |
| 4 | Packet Formats 1 of 3(?) | 05 Jan 2013 23:47:00 EST by Tom Ritter |
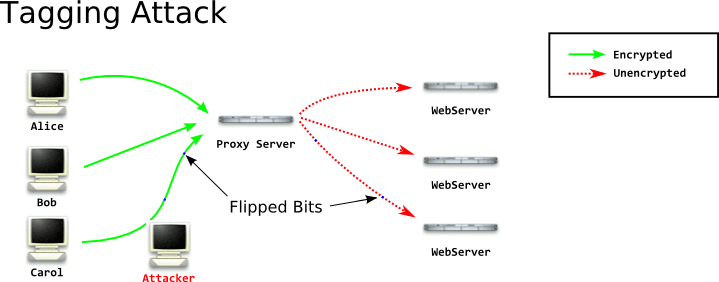
| 3 | Tagging Attacks | 05 Jan 2013 23:46:00 EST by Tom Ritter |
| 2 | Remailers We've Got | 05 Jan 2013 23:45:00 EST by Tom Ritter |
| 1 | What is a Remailer? | 05 Jan 2013 23:44:00 EST by Tom Ritter |
I put a lot of effort into them, and it goes into (what I think) are fairly complicated topics like tagging attacks, so I hope you like them!
required, hidden, gravatared
required, markdown enabled (help)
* item 2
* item 3
are treated like code:
if 1 * 2 < 3:
print "hello, world!"
are treated like code: